Frequently Asked Questions
To get ISO 27001 certification, an organization must develop and implement an Information Security Management System (ISMS) and then register for certification with an accredited body. The certification body will audit the ISMS to ensure it meets the standard's requirements.
ISO 27001 is an international standard that provides a framework for managing an organization's information security. It's also known as ISO/IEC 27001:2022.
The cost to get ISO 27001 certified can vary significantly depending on the size and complexity of your organization, including costs for implementation, consultancy, and the certification audit itself; with larger companies potentially incurring higher costs.
ISO 27001 audits are performed by competent and objective auditors who are certified and experienced in the standard. These auditors can be internal or external to the organization being audited.
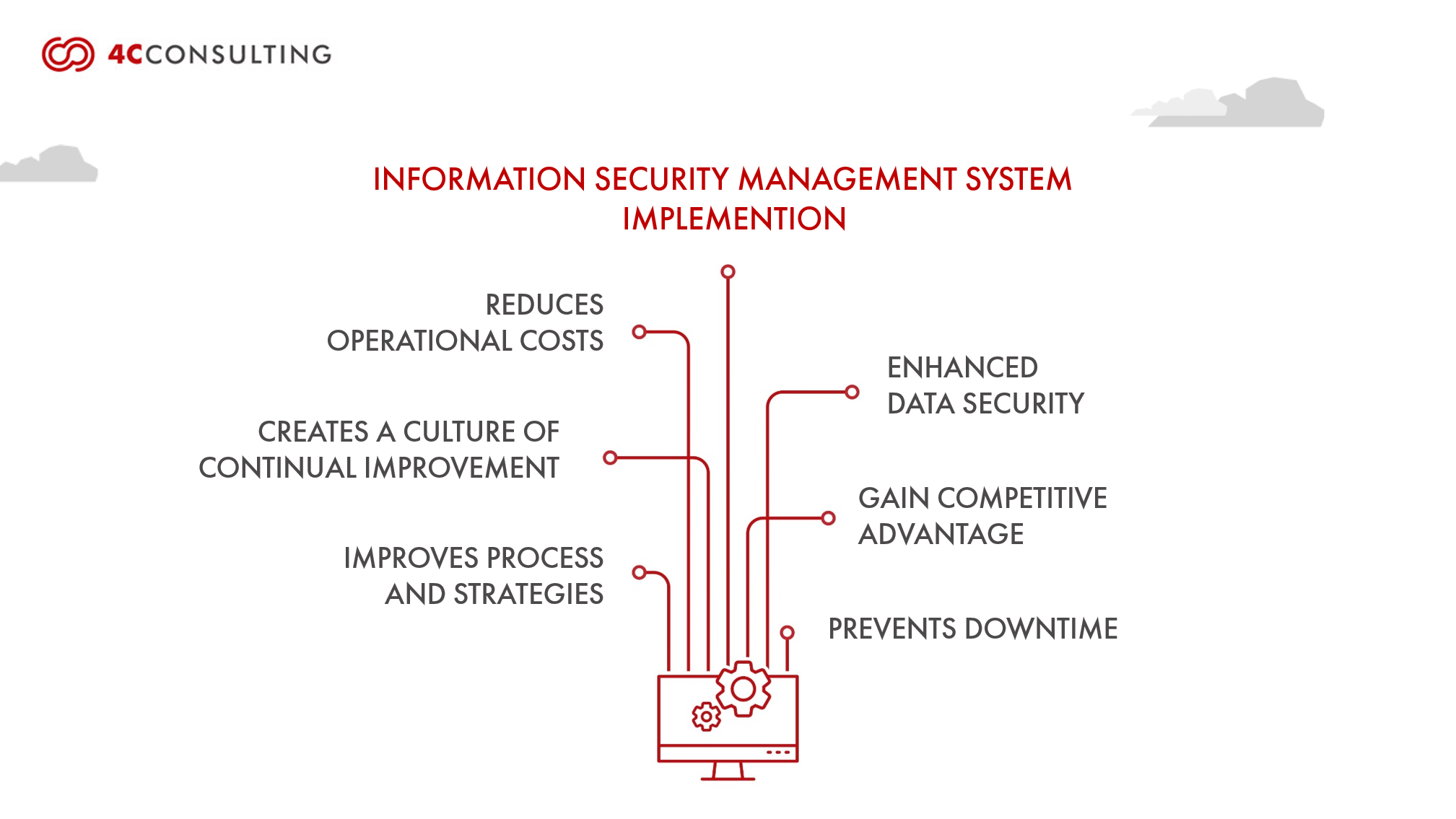
ISO 27001 is an information security standard that helps organizations protect their data and comply with legal regulations. It demonstrates your commitment to strong information security practice.
ISO 27001 controls are policies, procedures, and processes that organizations use to meet the security requirements of the framework. These controls are listed in Annex A of the ISO 27001 standard.